BEYOND GUT INSTINCT
Using Analysis of Competing Hypotheses in Malware Attribution
How structured analytic techniques can sharpen your threat intelligence and reduce cognitive bias
Introduction
In threat intelligence, we are constantly making judgments under uncertainty. Is this sample related to that campaign? Is this the work of a state-sponsored actor or a financially motivated criminal group? Did APT-X develop this tooling, or are we looking at shared infrastructure?
Too often, analysts fall into the trap of anchoring on the first plausible explanation that fits the evidence. We find a Korean-language string, note a targeting pattern consistent with DPRK interests, and declare attribution with unwarranted confidence. This is where Analysis of Competing Hypotheses (ACH) becomes invaluable.
Developed by Richards Heuer at the CIA, ACH is a structured analytic technique designed to mitigate cognitive biases by forcing analysts to systematically evaluate all reasonable hypotheses against all available evidence. Rather than asking "does the evidence support my theory?" we ask "which hypothesis is most consistent with the evidence, and which can we confidently eliminate?"
The following four scenarios demonstrate how ACH transforms ambiguous situations into defensible analytic judgments.
Matrix Legend:
Scenario 1: The Suspicious Overlap
Shared Tooling or Shared Actor?
The Situation
During analysis of a supply chain compromise targeting cryptocurrency firms, you recover a second-stage loader with several notable characteristics:
• Custom XOR-based string obfuscation matching a technique previously attributed to Lazarus Group
• C2 infrastructure hosted on a VPS provider commonly used by multiple threat actors
• A compilation timestamp consistent with UTC+9 working hours
• Code overlap (approximately 40% similarity) with publicly documented AppleJeus samples
• The same loader was observed three weeks earlier in an intrusion attributed to a different group (TraderTraitor) by another vendor
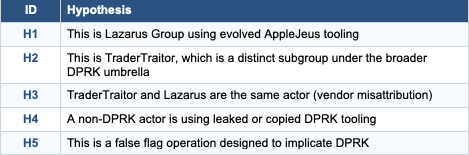
The Hypotheses
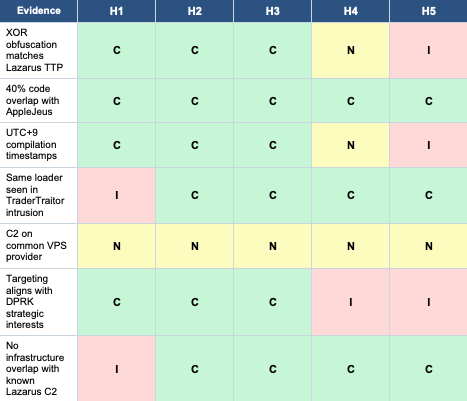
ACH Matrix
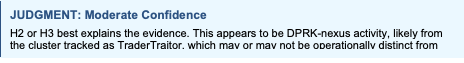
Analysis
H5 (false flag) accumulates the most inconsistencies. Creating a convincing false flag would require access to non-public tooling details and sustained operational patterns aligned with DPRK interests. H4 (non-DPRK actor) struggles with the targeting alignment and operational timing. The interesting competition is between H1, H2, and H3. The lack of infrastructure overlap with known Lazarus C2 is mildly inconsistent with H1 but consistent with both H2 and H3.
Scenario 2: The Outlier Sample
Evolution, New Actor, or Artifact?
The Situation
Your threat hunting team flags an unusual sample from a financial sector client. Initial triage reveals:
• A Go-based implant (the threat actor you track typically uses C++)
• Strings and comments in Russian (your tracked actor has historically shown Mandarin artifacts)
• Targeting and initial access vector matches your tracked actor's TTPs exactly
• The implant's command structure and tasking protocol are functionally identical to previously documented samples
• PDB path contains a username not previously observed
• Sample was compiled six months ago but only recently deployed
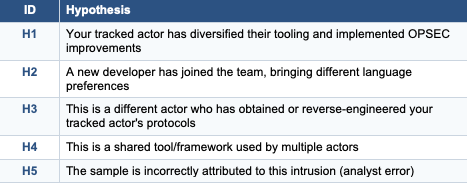
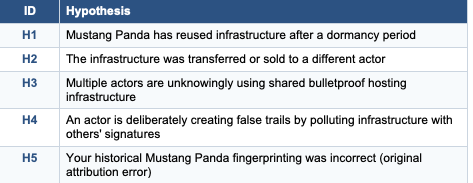
The Hypotheses
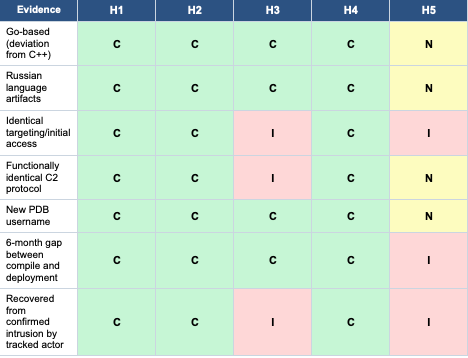
ACH Matrix
Analysis
H5 (analyst error) must be addressed first—if the sample association is incorrect, all other analysis is moot. H3 (different actor) accumulates significant inconsistencies. The functional identity of the C2 protocol is particularly damaging—reverse-engineering would likely produce functional equivalence with implementation differences. H1 and H2 are both highly consistent.
Scenario 3: The Infrastructure Puzzle
Convergence or Coincidence?
The Situation
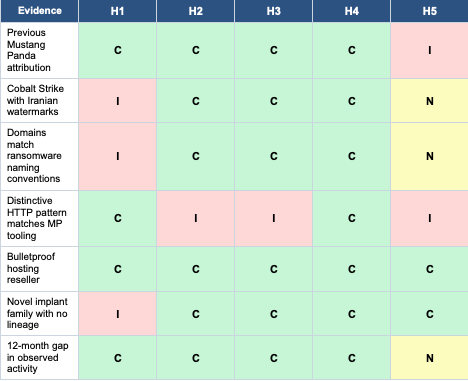
During infrastructure analysis, you identify a C2 server that presents a complex attribution picture:
• IP address previously flagged in reporting as Mustang Panda infrastructure (12 months ago)
• Same IP recently observed serving Cobalt Strike payloads configured with watermarks associated with a suspected Iranian actor
• Passive DNS shows the IP resolved to domains matching naming conventions used by a cybercriminal ransomware affiliate
• The server runs a distinctive HTTP response pattern you've previously fingerprinted as unique to Mustang Panda's custom tooling
• Let's Encrypt certificate with a registration email tied to a known bulletproof hosting reseller
• Current sample communicating with this IP is a novel implant family with no clear lineage
The Hypotheses
ACH Matrix
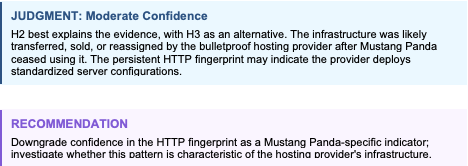
Analysis
The critical discriminating evidence is the HTTP response pattern. This fingerprint was based on server-side tooling, not network artifacts that could be spoofed. If this fingerprint is reliable, it strongly indicates continuity of the server-side component even if the actors using it have changed. H3 (shared infrastructure) is weakened by this—multiple actors sharing a server would be unusual, but multiple actors purchasing from the same reseller who deploys standardized tooling could explain the pattern.
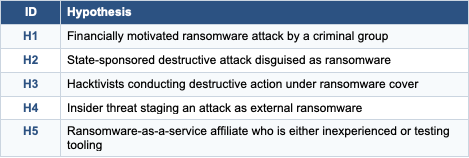
Scenario 4: The Wiper Dilemma
Ransomware or Sabotage?
The Situation
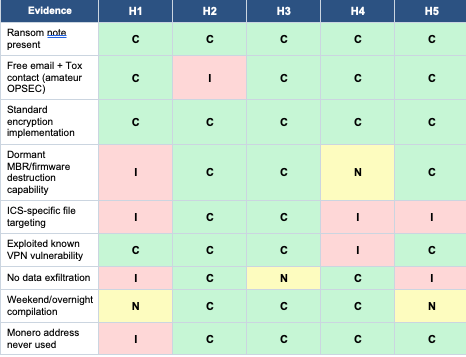
A client in the energy sector experiences a destructive attack. Your IR team recovers a sample that:
• Contains a ransom note demanding payment in Monero
• The ransom note includes a contact email on a free email provider and a Tox ID
• Implements file encryption using AES-256 with RSA key wrapping (standard ransomware pattern)
• Also contains functionality to overwrite MBR and corrupt firmware—functionality not called in observed execution
• Targets file extensions specific to industrial control system (ICS) engineering software
• Initial access was through a compromised VPN appliance with a known vulnerability
• No evidence of data exfiltration prior to encryption
• The Monero address has never received a transaction
The Hypotheses
ACH Matrix
Analysis
H1 (criminal ransomware) accumulates significant inconsistencies. Modern ransomware operations virtually always exfiltrate data for double-extortion leverage. The ICS-specific targeting and dormant destructive capabilities don't align with financial motivation. The unused Monero address suggests the payment mechanism was never intended to function. H4 (insider) is inconsistent with the VPN exploitation. The competition is between H2 (state sabotage) and H3 (hacktivist).
Conclusion: ACH as Intellectual Discipline
These scenarios illustrate ACH's core value: forcing analysts to confront disconfirming evidence rather than cherry-picking data that supports preferred conclusions.
In each case, ACH revealed:
1. Hidden assumptions — In Scenario 3, we discovered that a "high-confidence" fingerprint might actually characterize infrastructure providers rather than threat actors.
2. Intelligence gaps — Scenario 1 explicitly identified what additional collection would discriminate between remaining hypotheses.
3. Appropriate confidence levels — ACH prevents both overconfidence (Scenario 4's clear elimination of criminal ransomware) and false certainty (Scenario 2's acknowledged inability to distinguish between H1 and H2).
4. Alternative explanations — Scenario 2 could have easily resulted in a "new Russian actor" assessment if the analyst anchored on language artifacts.
ACH isn't a silver bullet. It requires intellectual honesty in hypothesis generation (deliberately including explanations you think are unlikely) and evidence evaluation (resisting the temptation to rationalize inconsistencies). But when applied rigorously, it transforms attribution from intuition into defensible analysis.
References
Heuer, Richards J., Jr. — Psychology of Intelligence Analysis (1999)
Heuer, Richards J., Jr. & Pherson, Randolph H. — Structured Analytic Techniques for Intelligence Analysis (3rd edition, 2020)
MITRE Engenuity & Center for Threat-Informed Defense — "Using Structured Analytic Techniques in Cyber Threat Intelligence" (white papers and presentations, 2022–2024)