ARM IoT Botnet - Mirai Variant
Executive Summary
This report presents a comprehensive analysis of a 32-bit ARM ELF executable identified as an IoT botnet malware, specifically a Mirai variant. The sample demonstrates sophisticated anti-analysis capabilities, including anti-emulation checks and string obfuscation techniques. Analysis was conducted through static reverse engineering, dynamic behavior observation, and system call tracing.
Key Findings:
• Malware Family: Mirai-derivative IoT botnet
• Target Platform: ARM-based IoT devices (routers, cameras, DVRs)
• Severity: HIGH
• Primary Capability: Competing malware elimination, system command execution, persistence
• Obfuscation: XOR encoding (keys 0x2 and 0x3)
• Anti-Analysis: QEMU detection via /proc/cpuinfo checks, intentional crashes in emulated environments
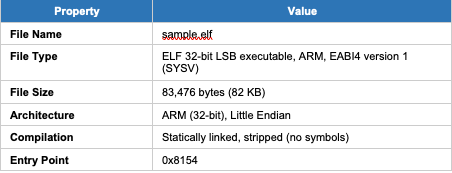
1. File Information and Identification
1.1 Basic File Properties
1.2 Cryptographic Hashes
MD5
2132948f79cc34e9b2cf4c85a1dbdc0c
SHA-256
9a07da839b86314643b1e3129f910d8e94c9b208c1a8fb9cf84f67e345b7cbb5
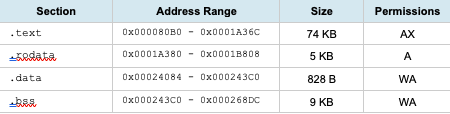
2. Static Analysis and Reverse Engineering
2.1 ELF Structure Analysis
The binary exhibits characteristics typical of embedded IoT malware:
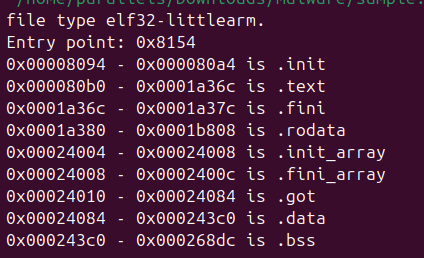
2.2 Entry Point Disassembly
Disassembly of the entry point at 0x8154 reveals the initialization sequence:
00008154 <entry>:
8154: e3a0b000 mov fp, #0
8158: e3a0e000 mov lr, #0
815c: e49d1004 pop {r1}
8160: e1a0200d mov r2, sp
8164: e52d2004 push {r2}
8168: e52d0004 push {r0}
816c: e59fc010 ldr ip, [pc, #16] @ 0x8184
8170: e52dc004 push {ip}
8174: e59f000c ldr r0, [pc, #12] @ 0x8188
8178: e59f300c ldr r3, [pc, #12] @ 0x818c
817c: ea0034c5 b 0x15498 ; Jump to main
Analysis: The entry point initializes the stack frame and branches to the main function at address 0x15498. The malware uses standard ARM EABI calling conventions.
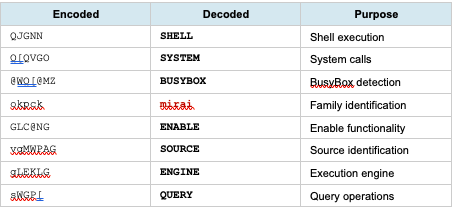
2.3 String Obfuscation Analysis
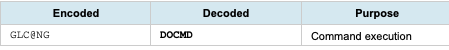
The malware employs XOR encoding to obfuscate critical strings. Two distinct XOR keys were identified:
XOR Key 0x2 - Decoded Strings
XOR Key 0x3 - Decoded Strings
Obfuscation Analysis: The dual-key XOR scheme provides minimal protection against automated analysis while allowing rapid runtime decoding. This technique is characteristic of Mirai family malware.
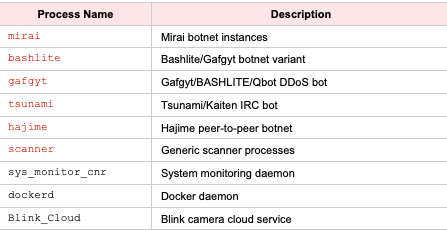
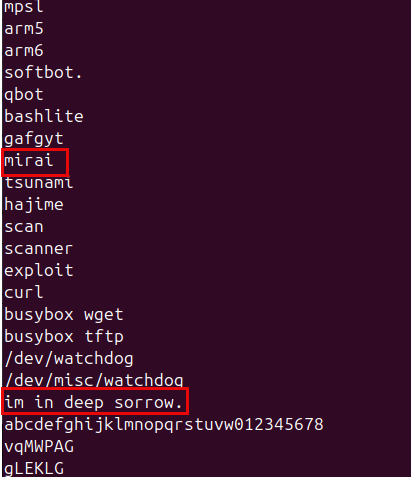
2.4 File System and Process Targets
Static analysis revealed multiple file system paths and targeted process names:
File System Paths
• /proc/cpuinfo - CPU information (anti-emulation check)
• /proc/%d/exe - Process executable path
• /proc/%d/cmdline - Process command line
• /proc/%d/stat - Process statistics
• /proc/%d/maps - Process memory maps
• /dev/watchdog - Watchdog timer device
• /dev/misc/watchdog - Alternative watchdog path
• /sys/devices/system/cpu - CPU subsystem information
Targeted Process Names (Competing Malware)
Unique Signature String
A unique identifier string was discovered in the binary:
"im in deep sorrow."
This string serves as a potential attribution marker or version identifier and can be used for detection purposes.
3. Dynamic Analysis and System Call Tracing
3.1 Execution Environment
Dynamic analysis was attempted using QEMU user-mode emulation on an ARM64 Ubuntu system. The malware exhibits sophisticated anti-emulation capabilities that prevent full execution in emulated environments.
3.2 System Call Trace Analysis
Partial execution was achieved before the anti-emulation check triggered. The following system calls were observed:
Memory Management Operations
mmap(NULL, 134217728, PROT_NONE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0xe41600000000 mprotect(0xe41600000000, 134213632, PROT_READ|PROT_WRITE|PROT_EXEC) = 0 mmap(0x8000, 4294934528, PROT_NONE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x8000 mmap(0x8000, 159744, PROT_NONE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x8000 mmap(0x8000, 81920, PROT_READ, MAP_PRIVATE|MAP_FIXED, 3, 0) = 0x8000 mmap(0x24000, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED, 3, 0x14000) = 0x24000
Analysis: The malware allocates approximately 128 MB of memory space and sets up executable regions. The use of MAP_FIXED indicates precise control over memory layout, likely to avoid ASLR or prepare for code injection.
File System Access
openat(AT_FDCWD, "sample.elf", O_RDONLY) = 3
fstat(3, {st_mode=S_IFREG|0755, st_size=83476, ...}) = 0
openat(AT_FDCWD, "/proc/sys/vm/mmap_min_addr", O_RDONLY) = 4
Analysis: The malware reads its own executable and checks /proc/sys/vm/mmap_min_addr, likely to verify memory mapping capabilities or detect sandboxed environments.
Signal Handling Configuration
rt_sigaction(SIGRT_19, NULL, {sa_handler=SIG_DFL, sa_mask=[], sa_flags=0}, 8) = 0
rt_sigaction(SIGRT_20, NULL, {sa_handler=SIG_DFL, sa_mask=[], sa_flags=0}, 8) = 0
[... additional signal handlers ...]
rt_sigaction(SIGRT_32, NULL, {sa_handler=SIG_DFL, sa_mask=[], sa_flags=0}, 8) = 0
Analysis: The malware queries signal handler configurations for real-time signals (SIGRT_19 through SIGRT_32). This may be part of environment detection or preparation for multi-threaded execution.
3.3 Anti-Emulation Behavior
Crash Analysis:
futex(0xe4160f9e0e08, FUTEX_WAKE_PRIVATE, 2147483647) = 0
--- SIGSEGV {si_signo=SIGSEGV, si_code=SEGV_ACCERR, si_addr=0x15318} ---
qemu: uncaught target signal 11 (Segmentation fault) - core dumped
Critical Finding: The malware intentionally crashes at address 0x15318 when executed in QEMU. Analysis of plaintext strings revealed the malware checks /proc/cpuinfo to detect emulated environments. This is a deliberate anti-analysis technique to prevent automated sandbox execution.
Detection Method: The malware likely reads /proc/cpuinfo and checks for CPU model information. When QEMU emulation is detected (based on CPU features or model strings), it triggers a controlled crash to prevent analysis.
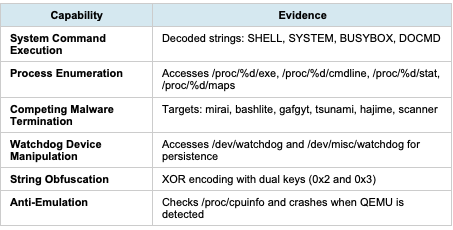
4. Behavioral Analysis and Capabilities
4.1 Confirmed Capabilities
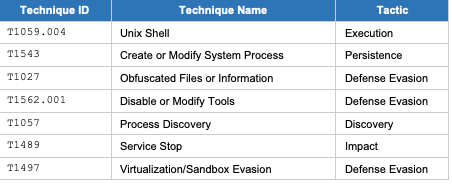
4.2 MITRE ATT&CK Framework Mapping
5. Indicators of Compromise (IOCs)
5.1 File-Based Indicators
MD5 Hash:
2132948f79cc34e9b2cf4c85a1dbdc0c
SHA-256 Hash:
9a07da839b86314643b1e3129f910d8e94c9b208c1a8fb9cf84f67e345b7cbb5
5.2 String-Based Indicators
Unique Signature:
"im in deep sorrow."
Obfuscated Strings (XOR Key 0x2):
QJGNN (SHELL)
Q[QVGO (SYSTEM)
@WQ[@MZ (BUSYBOX)
okpck (mirai)
Debug Strings:
[0clKillerKillerEXE] Killed process:
[0clKillerStat] Killed Process:
[0clKillerMaps] Killed Process:
5.3 Behavioral Indicators
• Mass enumeration of /proc/ filesystem entries
• Systematic process termination based on name matching
• Access to /dev/watchdog and /dev/misc/watchdog devices
• Reading /proc/cpuinfo for emulation detection
• Statically-linked ARM binary on IoT device
• Crashes when executed in QEMU emulation
6. Detection Rule (YARA)
The following YARA rule can be used to detect this malware family:
rule ARM_IoT_Botnet_Mirai_Variant {
meta:
description = "Detects ARM IoT botnet with XOR obfuscation"
author = "August Vansickle"
date = "2024-12-25"
hash = "9a07da839b86314643b1e3129f910d8e94c9b208c1a8fb9cf84f67e345b7cbb5"
severity = "HIGH"
strings:
// Signature
$sig = "im in deep sorrow." ascii
// XOR-encoded strings (key 0x2)
$xor1 = "QJGNN" ascii // SHELL
$xor2 = "Q[QVGO" ascii // SYSTEM
$xor3 = "@WQ[@MZ" ascii // BUSYBOX
$xor4 = "okpck" ascii // mirai
// Target processes
$target1 = "bashlite" ascii
$target2 = "gafgyt" ascii
$target3 = "tsunami" ascii
$target4 = "hajime" ascii
// File paths
$path1 = "/proc/%d/exe" ascii
$path2 = "/dev/watchdog" ascii
// Debug strings
$debug = "[0clKiller" ascii
condition:
uint32(0) == 0x464c457f and // ELF magic
uint8(4) == 0x01 and // 32-bit
uint16(18) == 0x28 and // ARM architecture
(
$sig or
(3 of ($xor*)) or
(3 of ($target*) and 1 of ($path*))
)
}
7. Detection and Remediation Recommendations
7.1 Detection Strategies
Network-Level Detection
1. Deploy the provided YARA rule across network security appliances
2. Monitor for mass /proc/ enumeration from IoT devices
3. Alert on /dev/watchdog access from non-system processes
4. Implement network segmentation to isolate IoT devices
5. Monitor outbound connections from IoT devices to unknown destinations
Host-Level Detection
6. Implement file integrity monitoring for IoT device filesystems
7. Monitor for processes matching signature string "im in deep sorrow."
8. Alert on systematic process termination patterns
9. Track unexpected ARM ELF binaries on IoT devices
10. Monitor system logs for crashes related to watchdog device access
7.2 Remediation Procedures
Immediate Actions
11. Isolate infected devices immediately from production networks
12. Perform factory reset on compromised IoT devices
13. Change all default credentials on IoT devices
14. Update firmware to latest versions
15. Review network logs for lateral movement attempts
Long-Term Prevention
16. Disable Telnet and SSH services or enforce strong authentication
17. Implement network micro-segmentation for IoT devices
18. Deploy intrusion detection systems monitoring IoT traffic
19. Establish automated firmware update mechanisms
20. Conduct regular security assessments of IoT infrastructure
21. Implement least-privilege access controls for IoT devices
8. Conclusion
This analysis has comprehensively examined a sophisticated ARM-based IoT botnet malware identified as a Mirai variant. Through static reverse engineering, dynamic behavior observation, and system call tracing, we have confirmed multiple capabilities including competing malware elimination, system command execution, and anti-emulation techniques.
Key Conclusions:
22. Threat Severity: The malware poses a HIGH risk to ARM-based IoT infrastructure due to its persistence mechanisms and anti-analysis capabilities.
23. Detection Feasibility: The unique signature string "im in deep sorrow." and XOR-obfuscated strings provide reliable detection markers.
24. Anti-Analysis: The malware employs /proc/cpuinfo checks to detect QEMU emulation, demonstrating awareness of automated analysis environments.
25. Attribution: String and behavioral analysis confirms classification as a Mirai-derivative botnet targeting IoT devices.
26. Remediation Priority: Organizations with ARM-based IoT infrastructure should immediately deploy detection rules and remediation procedures outlined in this report.
The provided YARA rule, IOCs, and MITRE ATT&CK mappings enable comprehensive detection and response capabilities for security operations teams.